Multiple Response
Identify one
or more choices that best complete the statement or answer the question.
|
|
|
1.
|
Developer tools can help with
|
|
|
2.
|
What happens during a SQLi attack?
|
|
|
3.
|
Client-server applications
|
|
|
4.
|
Which of the following actions can help you maintain your digital footprint?
|
|
|
5.
|
Some of the best ways to prevent or at least mitigate a SQLi attack are
to
|
|
|
6.
|
Using view page source allows you to quickly see the following:
|
|
|
7.
|
Which of the following are characteristics of a credible source online?
|
|
|
8.
|
Which of the following statements are true?
|
Multiple Choice
Identify the
choice that best completes the statement or answers the question.
|
|
|
9.
|
A database is always comprised of
a. | personally identifying information. | c. | lots of cryptographically stored
symbols. | b. | tables with rows and columns. | d. | lots of little
databases. |
|
|
|
10.
|
Which of the following is a benefit of the fault-tolerant nature of Internet
routing?
a. | The ability to use a hierarchical naming system to avoid naming
conflicts | c. | The ability to resolve errors in domain name system (DNS) lookups | b. | The ability to
provide data transmission even when some connections between routers have failed | d. | The ability to use multiple protocols such as
hypertext transfer protocol (HTTP), Internet protocol (IP), and simple mail transfer protocol (SMTP)
to transfer data. |
|
|
|
11.
|
What can you trust to be secure 100 percent of the time?
a. | Text messages | c. | Apps | b. | Emails | d. | None of these |
|
|
|
12.
|
Which of the following is true about jobs in the field of cybersecurity?
a. | There are a lot of unfilled positions in cybersecurity right now, but in the next few
years all of those positions will be filled. | c. | There are many unfilled
cybersecurity positions right now, and there will be even more unfilled positions in the next couple
of years. | b. | Right now there aren’t many unfilled cybersecurity positions, but there will be
more in the next couple of years. | d. | There are too many qualified cybersecurity professionals. There are no unfilled
positions now, and there won’t be any unfilled positions in the next few
years. |
|
|
|
13.
|
Why are cyber vulnerabilities unlikely to go away?
a. | The government won’t allow people to fix them. | c. | They are side effects of the
freedom and ease of communicating online. | b. | Criminals need them to steal
identities. | d. | They’re
protected in a secret base. |
|
|
|
14.
|
The size and complexity of networks grew enormously when:
a. | Only governments and universities owned computers | c. | The number of personal computers
greatly increased | b. | Spamware caused some computers to break
down | d. | The hacktivists
started using the internet |
|
|
|
15.
|
Which of these is a phising email?
a. | 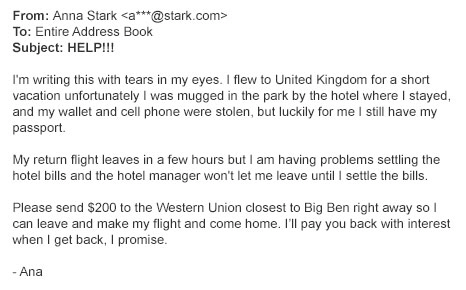 | b. | 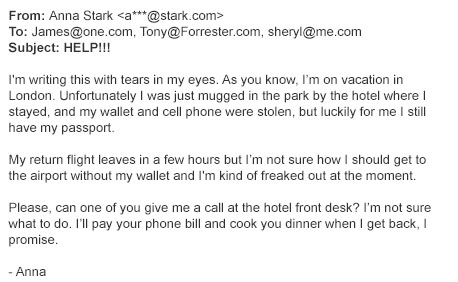 |
|
|
|
16.
|
A user enters a Web address in a browser, and a request for a file is sent to a
Web server. Which of the following best describes how the file is sent back to the user?
a. | The file is broken into packets and sent over a network. The user’s browser
must request each packet, in order, until all packets are received. | c. | The file is broken into packets and
sent over a network. The packets must be reassembled by the user’s computer when they are
received. If any packets are missing, the browser re-requests the missing
packets. | b. | The server attempts to connect directly to the user’s computer. If the
connection is successful, the entire file is sent at once. If the connection is unsuccessful, an
error message is sent to the user. | d. | The server repeatedly attempts to connect directly to the user’s computer until
a connection is made. Once the connection is made, the entire file is
sent. |
|
|
|
17.
|
Which aspect of the CIA triad ensures that data is protected from unauthorized
or unintentional alteration?
a. | Confidentiality | c. | Availability | b. | Integrity | d. | The CIA Triad is unrelated to data security
issues |
|
|
|
18.
|
Which of the following makes sure that each request is forwarded to its intended
recipient?
a. | Network | c. | Bits | b. | Router | d. | Computer
Systems |
|
|
|
19.
|
According to the domain name system (DNS), which of the following is a subdomain
of the domain example.com?
a. | about.example.com | c. | example.com.about | b. | example.com/about.html | d. | example.org |
|
|
|
20.
|
What information is contained in a packet?
a. | The entirety of a digital message | c. | A small part of a digital
message. | b. | The entirety of a digital message, and metadata about the message, including where it
came from and where it is going. | d. | A small part of a digital message, and metadata about the message, including where it
came from and where it is going. |
|
|
|
21.
|
What is a Distributed Denial of Service (DDoS) attack?
a. | An attempt by a government to deny Internet access to its citizens | c. | An attempt by one
user to deny service to another user by posting malicious material on a social
network | b. | An attempt to deny access to a website by flooding the website’s servers with
millions of requests from different computers | d. | An attempt by an Internet user to access
private information stored in a private database |
|
|
|
22.
|
Two computers are built by different manufacturers. One is running a Web server
and the other is running a Web browser. Which of the following best describes whether these two
computers can communicate with each other across the Internet?
a. | The computers cannot communicate, because different manufacturers use different
communication protocols. | c. | The computers can communicate directly only if the messages consist
of text. Other formats cannot be interpreted across computers. | b. | The computers can
communicate, but additional hardware is needed to convert data packets from one computer’s
protocol to the other computer’s protocol. | d. | The computers can communicate directly because
Internet communication uses standard protocols that are used by all computers on the
Internet. |
|
|
|
23.
|
A primary requirement for a good cryptographic hash function is that the
function should not produce too many collisions. A collision in a hash function is when:
a. | There are few inputs, but a lot of outputs. | c. | 2 inputs map to the same
output. | b. | 2 outputs come from the same input. | d. | There are few outputs, but a lot of
inputs. |
|
|
|
24.
|
To decrypt an encrypted message, pass the encrypted message and the _____ to the
decrypt function.
a. | cryptology | c. | key | b. | decrypted message | d. | ciphertext |
|
|
|
25.
|
Which of the following is a benefit of the fault-tolerant nature of Internet
routing?
a. | The ability to use a hierarchical naming system to avoid naming
conflicts | c. | The ability to use multiple protocols such as hypertext transfer protocol (HTTP),
Internet protocol (IP), and simple mail transfer protocol (SMTP) to transfer
data. | b. | The ability to resolve errors in domain name system (DNS) lookups | d. | The ability to provide data transmission even
when some connections between routers have failed |
|
|
|
26.
|
Which of these is regularly used for secure online communication?
a. | Caesar cipher | c. | Morse code | b. | Public-key cryptography | d. | Enigma code |
|
|
|
27.
|
What is the primary flaw with the Caesar Cipher and other substitution
ciphers?
a. | It could not be applied to all messages | c. | It could only be used in
English | b. | With enough frequency, a message could be decrypted | d. | There were too many options when encrypting a
message |
|
|
|
28.
|
Chris is on an online auction site trying to make a bid on a new computer. As he
tries to make a bid, the site crashes and he loses the auction. Which part of the CIA triad was
broken?
a. | Confidentiality | c. | Availability | b. | Integrity | d. | All of the
above |
|
|
|
29.
|
In cybersecurity, what does CIA stand for?
a. | Central Intelligence Agency | c. | Confidentiality, Integrity,
Availability | b. | Cybersecurity Investigation Agency | d. | Cybersecurity, Internet,
Accessibility |
|
|
|
30.
|
Which of these groups exploits cyber vulnerabilities?
a. | Criminals | c. | Hactivists | b. | Governments | d. | All of the
above |
|
|
|
31.
|
An IPv4 address has 32 bits, so there are 232 (over 4 billion)
possible IPv4 addresses. Since the Internet is gaining devices quickly, we will soon surpass
232 unique devices on the Internet.
In anticipation of all the new Internet
devices, we are in the process of switching to IPv6, which uses 128 bits for a single address.
That’s 96 extra bits to represent one address!
Which of the following statements
correctly describes how many more addresses will be possible to represent by switching from IPv4 to
IPv6?
a. | 96 more addresses can be represented with IPv6 | c. | 96 times as many addresses can be
represented with IPv6 | b. | 296 more addresses can be
represented with IPv6 | d. | 296 times as many addresses can be represented with
IPv6 |
|
|
|
32.
|
In a database, columns and rows correspond to
a. | attributes and records. | c. | tables and
names. | b. | 1s and 0s. | d. | SQLi and XSS. |
|
|
|
33.
|
What is the Internet of Things?
a. | The network of devices with the ability to connect and exchange data | c. | A term created to
describe the impact that increased connectivity has on data security | b. | A mechanism to
increase network of security by involving every connected device in the protection of a
network | d. | Social and economic
inequality related to access to and use of the Internet-connected
devices |
|
|
|
34.
|
Which of the following best explains what happens when a new device is connected
to the Internet?
a. | A device driver is assigned to the device. | c. | A packet number is assigned to the
device. | b. | An Internet Protocol (IP) address is assigned to the device. | d. | A Web site is assigned to the
device. |
|
|
|
35.
|
What is a network?
a. | A supercomputer | c. | An internet service provider | b. | A computer
vulnerability | d. | Interconnected computers or devices |
|
|
|
36.
|
A city government is attempting to reduce the digital divide between groups with
differing access to computing and the Internet.
Which of the following actions is LEAST likely
to be effective in this purpose?
a. | Holding basic computer classes at community centers | c. | Putting helpful tips for operating
computers on the city government website | b. | Providing free wireless Internet connections at
locations in low-income neighborhoods | d. | Requiring that every school and library have assistive devices that allow people with
disabilities to access computer resources |
|
|
|
37.
|
Which of these is a phishing site?
a. | 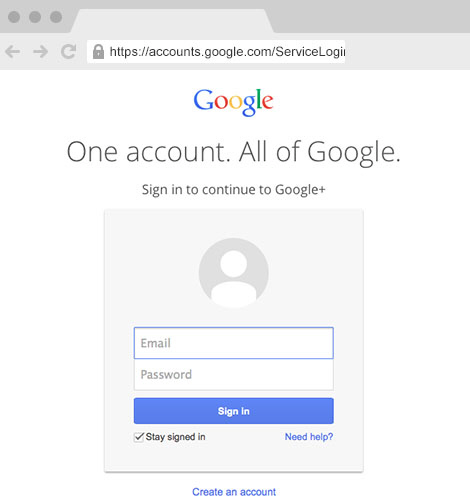 | b. | 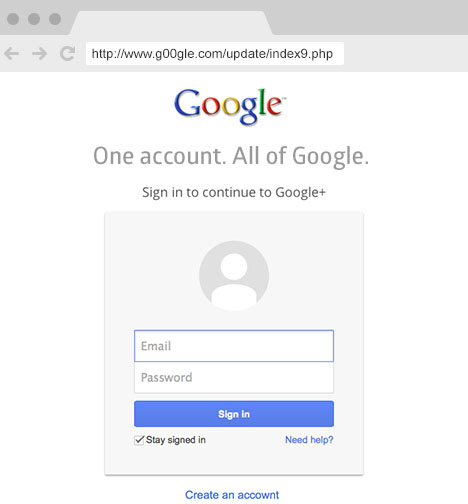 |
|
|
|
38.
|
Which of the following statements is true about creative credit and
copyright?
a. | There are exactly two copyright licenses. One allows free use of the content, and the
other only allows use of the content with payment and credit to the creator. | c. | Copyright licenses
range in how restrictive they are for reuse and modification of content. | b. | As long as you give
credit, you can use any content found online. | d. | An individual doesn’t own the content
they create unless they apply for a copyright license. |
|
|
|
39.
|
How can you tell if a website encrypts its traffic?
a. | Google it. | c. | All websites encrypt their traffic. | b. | Look for the lock
symbol in a URL. | d. | Encrypted
sites take longer to load. |
|
|
|
40.
|
What does redundancy mean in the context of Internet routing?
a. | Multiple paths exist between any two points | c. | Data sent over the Internet is sent
to the router with the lowest cost. | b. | For any two points on the Internet, there
exists only one path between them | d. | If a single router on a network breaks, the entire network
fails. |
|