Multiple Choice
Identify the
choice that best completes the statement or answers the question.
|
|
|
1.
|
Karel starts at Street 1 and Avenue 1, facing East. After calling the stairStep
function twice, where will Karel be and what direction will Karel be facing? (assume this is a
SuperKarel program and the world is 10x10 in size)
function stairStep()
{
move();
turnLeft();
move();
turnRight();
}
a. | Street 3, Avenue 3, Facing West | c. | Street 3, Avenue 3, Facing
East | b. | Street 2, Avenue 2, Facing North | d. | Street 4, Avenue 4, Facing
East |
|
|
|
2.
|
Which of the following statements are true about the Internet?
I - The
Internet connects devices and networks all over the world
II - Widespread use of the Internet has
led to concerns around privacy and copyright
III - The Internet helps people communicate
IV -
All of the world has access to the Internet
a. | I and II only | c. | I, III and IV | b. | I, II, III, IV | d. | I, II, and III |
|
|
|
3.
|
An online store uses 8-bit binary values to identify each unique item for sale.
The store plans to increase number of items it sells and is considering changing to 9-bit binary
values.
Which of the following best describes the result of using 9-bit values instead of
8-bit values?
a. | 9 more items can be uniquely identified | c. | 2 times as many items can be
uniquely identified | b. | 2 more items can be uniquely
identified | d. | 29
times as many items can be uniquely identified |
|
|
|
4.
|
Two computers are built by different manufacturers. One is running a Web server
and the other is running a Web browser. Which of the following best describes whether these two
computers can communicate with each other across the Internet?
a. | The computers can communicate directly because Internet communication uses standard
protocols that are used by all computers on the Internet. | c. | The computers can communicate, but
additional hardware is needed to convert data packets from one computer’s protocol to the other
computer’s protocol. | b. | The computers can communicate directly only if
the messages consist of text. Other formats cannot be interpreted across
computers. | d. | The computers
cannot communicate, because different manufacturers use different communication
protocols. |
|
|
|
5.
|
If Karel starts at Street 1 and Avenue 1, facing East, where will Karel be, and
what direction will Karel be facing after running the following code? (Assume the world is 10x10 in
size)
move();
turnLeft();
putBall();
turnLeft();
turnLeft();
turnLeft();
move();
turnLeft();
a. | Street 3, Avenue 1, Facing North | c. | Street 1, Avenue 3, Facing
South | b. | Street 1, Avenue 4, Facing North | d. | Street 1, Avenue 3, Facing
North |
|
|
|
6.
|
Suppose you have the following CSS rules:
p {
color: green;
}
.fire {
color: red;
}
#title
{
color: blue;
}
What font color will the following HTML element have
after being styled by the given CSS:
<p class="title">My First
Paragraph</p>
a. | red | c. | black | b. | green | d. | blue |
|
|
|
7.
|
Which binary value is equal to the decimal number 710?
a. | 11111112 | c. | 1112 | b. | 72 | d. | 1012 |
|
|
|
8.
|
Which of the following statements is something the operating system of a
computer is responsible for doing?
a. | Allowing the user to write programs. | c. | Managing memory allocation for all
applications. | b. | Providing a way for the user to create text documents. | d. | Allowing the user to access the
internet. |
|
|
|
9.
|
Which of the following best describes the difference between the domain and path
of a URL?
a. | The domain specifies where the browser’s request should be sent.
The path
specifies exactly what file is being requested. | c. | The domain specifies what kind of
file is being requested.
The path specifies the name of the file being
requested. | b. | The domain specifies the name of the file being requested.
The path specifies what
kind of file is being requested. | d. | The domain specifies exactly what file is being requested.
The path specifies
where the browser’s request should be sent. |
|
|
|
10.
|
An image is hosted
at
https://upload.wikimedia.org/wikipedia/commons/6/62/Big_and_little_dog.jpg
Which of the
following is the proper HTML code to display this image on your webpage?
a. | <img
src="https://upload.wikimedia.org/wikipedia/commons/6/62/Big_and_little_dog.jpg"></img> | c. | <img>https://upload.wikimedia.org/wikipedia/commons/6/62/Big_and_little_dog.jpg</img> | b. | <img
src="https://upload.wikimedia.org/wikipedia/commons/6/62/Big_and_little_dog.jpg"> | d. | <a
href="https://upload.wikimedia.org/wikipedia/commons/6/62/Big_and_little_dog.jpg">Image</a> |
|
|
|
11.
|
Suppose you are making a music streaming website and you want to make a page
that displays a user’s music library. Which of the following is the proper HTML code to
create the following table: 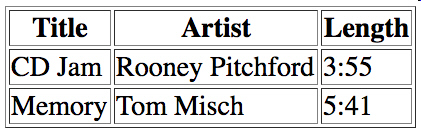 a. | <table border="1">
<tr>
<td>Title</td>
<td>Artist</td>
<td>Length</td>
</tr>
<tr>
<td>Memory</td>
<td>Tom
Misch</td>
<td>5:41</td>
</tr>
<tr>
<td>CD
Jam</td>
<td>Rooney
Pitchford</td>
<td>3:55</td>
</tr>
</table> | c. | <table
border="1">
<tr>
<th>Title</th>
<th>CD
Jam</th>
<th>Memory</th>
</tr>
<tr>
<td>Artist</td>
<td>Rooney
Pitchford</td>
<td>Tom
Misch</td>
</tr>
<tr>
<td>Length</td>
<td>3:55</td>
<td>5:41</td>
</tr>
</table> | b. | <table
border="1">
<tr>
<th>Title</th>
<th>Artist</th>
<th>Length</th>
</tr>
<tr>
<td>CD
Jam</td>
<td>Rooney
Pitchford</td>
<td>3:55</td>
</tr>
<tr>
<td>Memory</td>
<td>Tom
Misch</td>
<td>5:41</td>
</tr>
</table> | d. | <table
border="1">
<tr>
<th>Title</th>
<td>CD
Jam</td>
<td>Memory</td>
</tr>
<tr>
<th>Artist</th>
<td>Rooney
Pitchford</td>
<td>Tom
Misch</td>
</tr>
<tr>
<th>Length</th>
<td>3:55</td>
<td>5:41</td>
</tr>
</table> |
|
|
|
12.
|
In the following code, what would be a good Postcondition to write?
/*
Precondition: Karel is on a spot with a tennis ball facing East
* Postcondition:
...
*/
function getOnTop() {
turnLeft();
move();
turnRight();
}
a. | Karel ends one spot above a tennis ball facing East | c. | Karel is facing
East | b. | Karel is on a spot with a tennis ball facing north | d. | Karel is on the same position but on top of a
ball |
|
|
|
13.
|
Which of the following choices lists the three main components of a
computer’s hardware?
a. | CPU, Flash memory, Processor | c. | CPU, Memory,
Motherboard | b. | Input devices, Output devices, Motherboard | d. | Processor, Binary,
RAM |
|
|
|
14.
|
Which of the following describes a task effectively broken into smaller
parts?
I. Building a tree house by making a building plan, getting supplies and tools, and
creating the base
II. Reading a book on programming
III. Comparing different walking
shoes
a. | I and II | c. | I only | b. | II and III | d. | I, II, and III |
|
|
|
15.
|
How many different values can be represented using 4 bits?
a. | 8 different values | c. | 4 different values | b. | 16 different values | d. | 32 different
values |
|
|
|
16.
|
A student is transferring photos from her camera to her computer. The student
notices that the saved photos on her computer are lower quality than the original raw photo on her
camera.
Which of the following could be a possible explanation for the difference in image
quality?
a. | Some information is lost every time a file is saved on a computer. | c. | The saved image
files were compressed with a lossy compression technique. | b. | The saved image
files were compressed with a lossless compression technique. | d. | The saved image files were not compressed
properly. |
|
|
|
17.
|
Karel the Dog is instructed to move forward three spaces. Then, if Karel is
standing on a ball, Karel will turn left and move forward two spaces. Otherwise, Karel will turn
around and move forward three spaces. Given the starting point below, where will Karel end
up? Starting Point: 
|
|
|
18.
|
What is the domain of this URL:
www.example.com/home.html
a. | www | c. | HTML | b. | home.html | d. | example.com |
|
|
|
19.
|
Which of the following is the correct way to define a turnRight function in
Karel?
a. | function turnRight() {
turnLeft();
turnLeft();
turnLeft();
} | c. | turnRight function()
{
turnLeft();
turnLeft();
turnLeft();
} | b. | function turnRight() {
turnRight();
turnRight();
turnRight();
} | d. | function turnright {
turnLeft();
turnLeft();
turnLeft();
} |
|
|
|
20.
|
What is generated from the following HTML
code:
<h1>Hello</h1>
<h3>Hello</h3>
<h6>Hello</h6>
a. | Hello
Hello
Hello | c. | Hello
Hello
Hello | b. | Hello
Hello
Hello | d. | Hello
Hello
Hello |
|
|
|
21.
|
What is top down design?
a. | Top down design is a way to use loops and if statements to decompose the
problem | c. | Top down design is a way of designing your program by starting with the biggest
problem and breaking it down into smaller and smaller pieces that are easier to
solve. | b. | Top down design is a way that you can create designs on a computer to put on a web
page | d. | Top down design is a
way of designing your programs starting with the individual commands
first |
|
|
|
22.
|
A news website uses 32-bit integers to count the number of times an article has
been viewed.
The website is becoming more popular, and expects some of the articles to exceed
the number of views that can be represented with 32 bits. In anticipation of this, the website is
planning to change to 64-bit integers for the view counter.
Which of the following best
describes the result of using 64-bit integers instead of 32-bit integers?
a. | 2 times as many values can be represented | c. | 322 times as many values
can be represented | b. | 32 times as many values can be
represented | d. | 232
times as many values can be represented |
|
|
|
23.
|
Which of the following are examples of encoding information?
I. Every item
for sale in a store has a corresponding barcode number
II. Areas within the United States being
assigned a zip code
III. Students at a school having a unique student identification number
a. | I only | c. | I and II only | b. | II and III only | d. | I, II, and III |
|
|
|
24.
|
Suppose we have the following function that modifies a pixel and returns the
result:
var RED = 0;
var GREEN = 1;
var BLUE = 2;
function filter(pixel)
{
pixel[RED] = 255 - pixel[RED];
pixel[GREEN] = 255 - pixel[GREEN];
pixel[BLUE] =
255 - pixel[BLUE];
return pixel;
}
Which of the following
best describes the result of applying this filter to every pixel in the image?
a. | The image will be grayscaled to a black and white image. | c. | The image will be
inverted, bright pixels will become dark and dark pixels will become bright. | b. | The image will look
slightly brighter. | d. | The
image will look slightly darker. |
|
|
|
25.
|
ASCII is a character encoding scheme that uses a numeric value to represent each
character. For example, the uppercase letter ‘G’ is represented by the binary
(base 2) value 0100 0111, which is equivalent to the decimal (base 10) value 71. A subset of
characters and their corresponding ASCII values are shown in the table below: 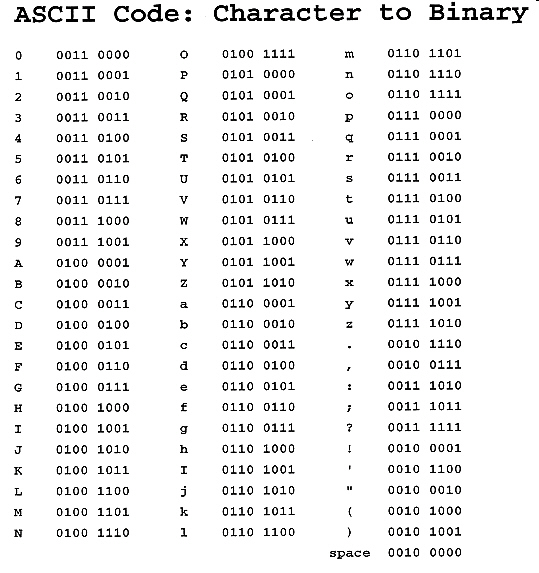 ASCII
characters can also be represented by hexadecimal (base 16) numbers. According to the ASCII character
encoding, which of the following characters is represented by the hexadecimal (base 16) number
6E 16
|
|
|
26.
|
The RGB encoding scheme encodes a color using 24 bit sequences. The first 8 bits
encode the amount of red in the color, the next 8 bits encode the amount of green in the color, and
the last 8 bits encode the amount of blue in the color.
Which of the following is a true
statement about the color encoded by this binary sequence:
1110 1001
0111 1100
0000
1111
a. | This color is mostly red. | c. | This color is mostly
green. | b. | This color is mostly blue. | d. | This color has no blue in it. |
|
|
|
27.
|
CSS rules have a selector that defines which HTML elements the rule applies
to.
We’ve learned about the following CSS Selectors:
Select by tag name
Select
by class name
Select by id name
Which of the following ranks the selectors from highest
priority to lowest priority?
a. | Select by id name, select by tag name, select by class name | c. | Select by id name,
select by class name, select by tag name | b. | Select by tag name, select by class name,
select by id name | d. | Select by
class name, select by id name, select by tag name |
|
|
|
28.
|
In this code, how many times is the dance function called and how many times is
it defined?
function start() {
move();
dance();
move();
move();
turnLeft();
dance();
dance();
}
function
dance() {
turnLeft();
move();
turnLeft();
turnLeft();
move();
turnLeft();
}
a. | Called 3 times, defined 3 times | c. | Called 1 time, defined 3
times | b. | Called 3 times, defined 1 time | d. | Called 1 time, defined 1
time |
|
|
|
29.
|
Which of the following is the proper format for an HTML tag?
a. | <h1 Content Affected by Tag /> | c. | <h1>Content Affected by
Tag</h1> | b. | >h1<Content Affected by Tag >/h1< | d. | <h1>Content Affected by
Tag<h1> |
|
|
|
30.
|
Which of the following are true statements about digital certificates in Web
browsers?
I. Digital certificates are used to verify the ownership of encrypted keys used in
secure communication.
II. Digital certificates are used to verify that the connection to a Web
site is fault tolerant.
a. | Neither I nor II | c. | I and II | b. | I only | d. | II only |
|
|
|
31.
|
An IPv4 address has 32 bits, so there are 232 (over 4 billion) possible IPv4
addresses. Since the Internet is gaining devices quickly, we will soon surpass 232 unique devices on
the Internet.
In anticipation of all the new Internet devices, we are in the process of
switching to IPv6, which uses 128 bits for a single address. That’s 96 extra bits to represent
one address!
Which of the following statements correctly describes how many more addresses
will be possible to represent by switching from IPv4 to IPv6?
a. | 96 more addresses can be represented with IPv6 | c. | 296 times as many
addresses can be represented with IPv6 | b. | 296 more addresses can be
represented with IPv6 | d. | 96
times as many addresses can be represented with IPv6 |
|
|
|
32.
|
Which of the following is a valid CSS rule?
a. | h1 {
color: blue;
} | c. | h1 {
color="blue";
} | b. | h1 {
color=blue;
} | d. | <h1>
{
color: blue;
} |
|
|
|
33.
|
Which of the following is an application of Artificial Intelligence?
a. | Game AI’s | c. | Recognizing handwriting | b. | All of the choices
here | d. | Foreign language
translation |
|
|
|
34.
|
Which number system is used to store information digitally in a computer?
a. | Binary (base 2) | c. | Octal (base 8) | b. | Hexadecimal (base 16) | d. | Decimal (base
10) |
|
|
|
35.
|
Which of the following is an example of an HTML tag?
a. | class="animal" | c. | text-align:
left; | b. | <h3> | d. | color: blue; |
|
|
|
36.
|
Karel starts at Street 1, Avenue 1, facing East in a 5x5 world. What will happen
after this code
runs?
move();
putBall();
move();
move();
move();
move();
move();
a. | This code won’t run because of a syntax error | c. | Karel will end on Street 1, Avenue
2 | b. | Karel will end on Street 1, Avenue 7 | d. | Karel will crash into a
wall |
|
|
|
37.
|
What is the decimal value of 11112?
a. | 1510 | c. | 1310 | b. | 1.10110 | d. | 1210 |
|
|
|
38.
|
Which of the following statements are true about styling your web pages with
CSS:
I. Styling with CSS is more scalable than using style= on each HTML tag that you want to
style
II. You can create styles with CSS that are not possible using style= on an HTML tag
a. | Neither I nor II | c. | I and II | b. | II only | d. | I only |
|
|
|
39.
|
What is wrong with this for loop?
for (var i = 0, i < 10, i + 1)
{
move();
}
a. | Both | c. | The for loop uses commas instead of semicolons | b. | It should say i++
instead of i + 1 | d. | Neither
|
|
|
|
40.
|
Consider the following numbers:
The decimal value 1010
The
binary value 10012
Hexadecimal value C16
Which of the following lists the
numbers in order from least to greatest?
a. | C, 1001, 10 | c. | 10, 1001, C | b. | 10, C, 1001 | d. | 1001, 10, C |
|
|
|
41.
|
Which of the following is LEAST likely to indicate a phishing attack?
a. | An email from your water utility company asks you to enter your date of birth and
social security number for verification purposes. | c. | An email indicates you have won
money, and asks you to enter your bank account number so the money can be
transferred | b. | An email from your bank asks you to call the number on your card to verify a
transaction. | d. | An email from
a website asks that you click on a link to reset your password. |
|
|
|
42.
|
Which of the following classifies as metadata about a webpage?
a. | The tags that make up the body of the webpage | c. | A list on a
webpage | b. | A table on a webpage | d. | The title of the webpage |
|
|
|
43.
|
Which of the following would pose the greatest threat to a user’s personal
privacy if it were to be leaked to the public?
a. | The user’s public key used for encryption | c. | The user’s browser
cookies | b. | The IP address of the user’s computer | d. | The user’s email
address |
|
|
|
44.
|
A city government is attempting to reduce the digital divide between groups with
differing access to computing and the Internet.
Which of the following actions is LEAST likely
to be effective in this purpose?
a. | Holding basic computer classes at community centers | c. | Putting helpful tips for operating
computers on the city government website | b. | Requiring that every school and library have
assistive devices that allow people with disabilities to access computer
resources | d. | Providing free
wireless Internet connections at locations in low-income
neighborhoods |
|
|
|
45.
|
A user enters a Web address in a browser, and a request for a file is sent to a
Web server. Which of the following best describes how the file is sent back to the user?
a. | The file is broken into packets and sent over a network. The packets must be
reassembled by the user’s computer when they are received. If any packets are missing, the
browser re-requests the missing packets. | c. | The server repeatedly attempts to
connect directly to the user’s computer until a connection is made. Once the connection is
made, the entire file is sent. | b. | The server attempts to connect directly to the
user’s computer. If the connection is successful, the entire file is sent at once. If the
connection is unsuccessful, an error message is sent to the user. | d. | The file is broken into packets and sent over a
network. The user’s browser must request each packet, in order, until all packets are
received. |
|
|
|
46.
|
If x represents the area of the number line colored blue, which inequality
accurately reflects the value of x? 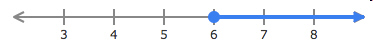 a. | x > 6 | c. | x >= 6 | b. | x <= 6 | d. | x < 6 |
|
|
|
47.
|
Which of the following is a true statement about data compression?
a. | Sending a compressed version of a file ensures that no one can read the contents of
the file except for the intended recipient. | c. | There are trade-offs involved in
choosing a compression technique for storing and transmitting data. | b. | Data compression is
only useful for files being transmitted over the Internet. | d. | Regardless of the compression technique being
used, once a data file is compressed, it cannot be restored back to its original
state. |
|
|
|
48.
|
Which of the following devices is the device that connects all of the physical
components of a computer together?
a. | Memory | c. | Motherboard | b. | CPU | d. | Logic |
|
|
|
49.
|
A computer program uses 3 bits to represent integers. When the program adds the
decimal (base 10) numbers 6 and 2, the result is 0. Which of the following is the best explanation
for this result?
a. | An overflow error occurred. | c. | The result was affected by lossy
data compression. | b. | An off-by-one error
occurred. | d. | A round-off error
occurred. |
|
|
|
50.
|
How many different digits are used in the Hexadecimal number system?
|