Multiple Choice
Identify the
choice that best completes the statement or answers the question.
|
|
|
1.
|
What is a possible remedy if your system hangs at
odd times or during the boot?
a. | Install new CMOS RAM | c. | Flash the BIOS/UEFI | b. | Remove the TPM chip | d. | Format the hard
disk |
|
|
|
2.
|
What must your motherboard have to use BitLocker
Encryption in Windows 7/8/10 which will ensure that your hard drive cannot be used in another
computer?
a. | LoJack | c. | Encrypted USB | b. | BIOS/UEFI password | d. | TPM chip |
|
|
|
3.
|
You decide to add three new hard drives to your computer so that you can
increase the amount of storage on it. When you install the hard drives, you find enough SATA
connections on the motherboard, but it is short one SATA power connector.
What is the easiest way to add a SATA power connector to the
system?
a. | Purchase a new power supply. | c. | Use the Molex
connector. | b. | Use a Molex to SATA power adapter. | d. | You will not be able to add the SATA hard
drive. |
|
|
|
4.
|
Where must virtualization be enabled for VM (virtual
machine) software to work?
a. | Windows Control Panel | c. | TPM chip | b. | BIOS/UEFI | d. | Jumper |
|
|
|
5.
|
Which of the following represents a method for
accessing the BIOS/UEFI setup program?
a. | Boot Windows and go to Control Panel | c. | Press a key or combination of keys
during the BIOS/UEFI POST | b. | Set a motherboard jumper and start the
computer | d. | Boot to the BIOS
setup floppy disk |
|
|
|
6.
|
According to the text, today’s DIMMs use what
size data path?
a. | 16-bit | c. | 64-bit | b. | 32-bit | d. | 128-bit |
|
|
|
7.
|
Landon starts his computer and receives the error message, “Hard drive is
not found.” In a panic, he calls you because he did not back up his data and has numerous
important files on his hard drive. During your investigation, Landon tells you he was watching a
movie on his computer the previous night.
What might be the problem with Landon’s
computer?
a. | CMOS RAM has lost power and reset to defaults | c. | POST failed | b. | Boot priority is set
to the DVD drive | d. | Motherboard needs to be replaced |
|
|
|
8.
|
Over the past week, every time Larry has started his computer, he has noticed
that the time is not correct. Larry didn’t consider this a problem because his computer was
working properly. However, now Larry has decided that he should investigate why the time is not
accurate.
?3?
What can you tell Larry to check to find
out why the clock does not keep the right time?
a. | POST is failing | c. | The motherboard is going bad and needs to be
replaced | b. | The internal time clock is malfunctioning | d. | The CMOS battery is bad and needs to be
replaced |
|
|
|
9.
|
Paul is playing a game when his computer shuts down unexpectedly. Paul has
noticed recently that his fans are running very loud. When Paul turns his computer back on, it starts
to boot and then shuts off again.
?3?
What is a possible problem with Paul’s computer?
a. | Windows is not installed | c. | Hard drive is
failing | b. | Fan drivers are not working | d. | Computer is overheating |
|
|
|
10.
|
Nick is working on a new graphic for one of his company’s clients and is
having an issue with the color on his screen. The client wants the graphic to include a very bright
red color, but Nick can’t seem to find the right color on his screen. He seems to have the
color perfect on the screen, but when he tries to print the graphic, the color seems to fade. He has
checked the printer, and it works fine.
What will help Nick see on the screen the color that
he is printing?
a. | Adjust the resolution. | c. | Adjust the refresh rate. | b. | Calibrate the
display color. | d. | Update the
video card drivers. |
|
|
|
11.
|
Terry is having a problem with his computer screen. He said the screen looks
distorted. When you go to check his monitor, you notice that the icons on the desktop appear to be
tall and skinny.
What is the common cause of this
problem?
a. | Font size has been set too high. | c. | Refresh rate of the video card is
out of sync with the monitor’s refresh rate. | b. | Computer’s resolution has been set too
low. | d. | ClearType setting is
enabled. |
|
|
|
12.
|
Roger purchased a new laptop computer and wants to connect it to a second
monitor. The monitor has a DVI and HDMI connection on the back, but his laptop only has a Mini
DisplayPort connection.
?3?
Which cable should Roger purchase?
|
|
|
13.
|
You have been tasked with configuring a SOHO network in which all ports on the
public untrusted network will be forwarded to one workstation connected to the LAN.
Which of the following features will you configure on the
SOHO router to accomplish this task?
a. | Port forwarding | c. | Demilitarized zone | b. | MAC filtering | d. | Quality of
service |
|
|
|
14.
|
What command line utility can be used to repair the
BCD on a Windows installation?
a. | chkdsk | c. | dfrgui | b. | diskpart | d. | bootrec |
|
|
|
15.
|
Jordan has been asked to help his company find a way to allow all the workers to
log on to computers securely but without using a user name and password. The CIO wants everyone use
face recognition software.
What
peripheral will be needed on each computer to allow the workers to log on using face recognition
software?
a. | Fingerprint reader | c. | Camera or webcam | b. | Face recognition reader | d. | Optical drive |
|
|
|
16.
|
When you are ordering a standard thick client computer for a normal business
user, what should you check before ordering the computer?
a. | Amount of RAM. | c. | Speed of CPU. | b. | Meet requirements for the
OS. | d. | Amount of storage
available. |
|
|
|
17.
|
Heather’s computer display is having a problem in which the desktop seems
to be shifting. She has sent you a picture of the problem.
?3?
What could be causing this problem on Heather’s
monitor? 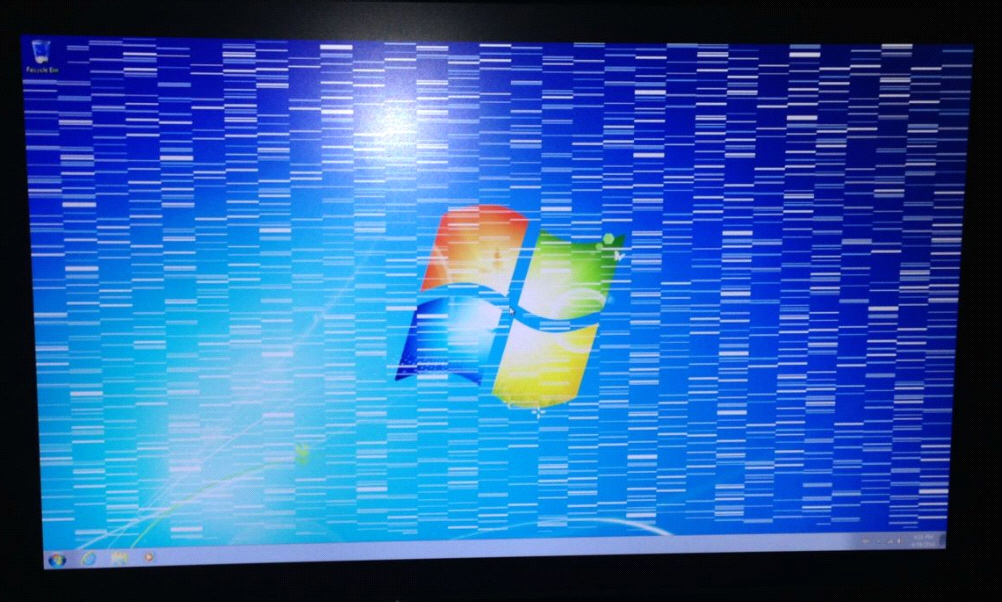 a. | Video cable not properly seated. | c. | Not enough video
memory. | b. | Refresh rate out of specification. | d. | GPU on video card
overheating. |
|
|
|
18.
|
A manager in a small office is asking if it is possible to limit network access
to a particular website during business hours. Apparently, several users are spending an excessive
amount of time on the site preventing them from completing their work-related tasks.
Which of the following is the best solution to accomplish the
request from the manager while not limiting access to other websites?
a. | Implement MAC filtering on the SOHO router for the PCs that are accessing the
site. | c. | Configure a firewall with content filtering on the PCs of users who are visiting the
site. | b. | Implement a blacklist on the firewall and add the site the users are
visiting. | d. | Configure a
firewall and add the site the users are visiting to the whitelist. |
|
|
|
19.
|
John just bought a used iPad from a friend who had lost the charging cable. John
notices that the cable is like the charging cable for his Android smartphone, though it is not quite
the same.
What type of cable will John need to purchase to replace the iPad’s
charger cable?
a. | Mini HDMI | c. | USB C | b. | Lightning | d. | Micro USB |
|
|
|
20.
|
A smartphone user entered an incorrect passcode on his phone several times in a
row, which locked the device.
Which of the following steps should the user take
first?
a. | Disable full device encryption. | c. | Wait a few minutes for the phone to
automatically unlock. | b. | Turn off multifactor
authentication. | d. | Perform a
reset on the device. |
|
|
|
21.
|
A technician is troubleshooting a printer connected to a computer via USB. The
printer will print using the controls at the printer but fails to print from the
computer.
Which of the following steps should be taken next?
a. | Make sure printing paper is installed. | c. | Verify the USB cable is
attached. | b. | Verify the printer is powered on. | d. | Check for low memory errors on the
printer. |
|
|
|
22.
|
Which of the following could be a major concern for implementing cloud computing
for business-critical services?
a. | An intermittent or unavailable Internet connection. | c. | Being charged for computing
services that go unused. | b. | A cloud provider’s inability to scale up
or down. | d. | Incompatible
software, hardware, or operating systems. |
|
|
|
23.
|
A server provides the necessary IP configuration to your network host so the
host can communicate on the network. If this service malfunctions, your device will not be able to
utilize the network.
What server provides this service?
a. | Syslog server | c. | DNS server | b. | Proxy server | d. | DHCP server |
|
|
|
24.
|
You are troubleshooting a Windows workstation that is having problems
communicating with the host at IP address 1.2.3.4.
What utility will you use at the
command line to determine where the communication is stopping?
a. | ipconfig /all | c. | tracert 1.2.3.4 | b. | netstat | d. | ping 1.2.3.4 |
|
|
|
25.
|
A mobile device user has tried to install a new app numerous times without
success. She has closed all unused apps, disabled live wallpapers, and restarted the device in an
attempt to get the app to install.
Which of the following steps should the user take
next?
a. | Check for sufficient available storage space. | c. | Back up all user data and perform a
factory reset. | b. | Disable full device encryption. | d. | Generate a new public
key. |
|
|
|
26.
|
Angela recently purchased a new Android smartphone. While purchasing the phone,
Angela was told that she would need to set up a new email account for the phone.
Which
commercial email provider should Angela use for her new Android phone?
a. | Microsoft Exchange Online | c. | Gmail | b. | Yahoo!
Mail | d. | iCloud |
|
|
|
27.
|
Which of the following indicates the most concise abbreviation of the IPv6
address FEFE:0000:0000:0000:0002:0000:0000:0001?
a. | FEFE:0:0:0:2:0:0:1 | c. | FEFE::2:0:0:1 | b. | FEFE::0002:0000:0000:0001 | d. | FEFE::2::1 |
|
|
|
28.
|
Your company received a call from a historical society inquiring about the
possibility of networking a two-century-old building with no existing network. In 1924, someone added
electrical outlets to the building, but the layout and design of the building prohibits adding any
additional copper or fiber cable. You completed a wireless site survey and concluded that wireless
networking is out of the question and will not properly function due to environmental
interference.
Which of the following could be used to network
this building?
|
|
|
29.
|
You are troubleshooting a mobile device that will not pair with a Bluetooth
headset. The device was functioning properly with the headset until a recent corporate-wide OS
update. No other mobile devices in the organization are exhibiting this issue with Bluetooth
headsets.
Which of the following is the first step you will take to resolve this
issue?
a. | Reset the network settings in the mobile device Settings app. | c. | Forget all Wi-Fi
networks on the mobile device | b. | Replace the Bluetooth headset with a new
pair. | d. | Update the radio
firmware in the mobile device. |
|
|
|
30.
|
A small bank with several regional branches is searching for a solution to
consolidate its business services into a single site with centralized management. The service should
provide secure resources for use by the bank, and these resources must be isolated from any other
organization using the same service provider.
Which of the following will best meet the
needs of the bank?
a. | Community cloud | c. | Public cloud | b. | Hybrid cloud | d. | Private cloud |
|
Multiple Response
Identify one
or more choices that best complete the statement or answer the question.
|
|
|
31.
|
A Windows computer is shared between several users, each with his own local user
account. Each user has his own dedicated, uniquely configured VM stored in a public folder on the
computer.
Which of the following steps should be taken to secure the VMs so no user can
copy or delete another user’s VM files? (Select TWO.)
|
|
|
32.
|
The accounting department moved its network-attached printer from one side of
the office to a more centralized location, making the printer much more accessible to all accounting
users. Since the move, the users have not been able to print to the printer. The printer powers on
and shows it is ready to accept print jobs. The printer configuration page shows the following
output.  You
disconnect the patch cable from the keystone jack at the new location and move the printer and cable
to reconnect it at the original location. The printer begins printing the jobs that failed to print
earlier. Which of the following are the most likely reasons for the printer failing to
print at the new location? (Select TWO.)
|
|
|
33.
|
Molly, a technician, has been tasked with researching an emulator for the
software developers to test cross-platform applications on various PCs and a variety of mobile
devices.
Which of the following will be a required step in selecting an emulator?
(Select TWO.)
|
|
|
34.
|
Which of the following are secure protocols, ports, services, or applications?
(Select TWO.)
|
|
|
35.
|
What methods are used to assign TCP/IP parameters to network hosts? (Select
TWO.)
|
|
|
36.
|
A mobile device user is having problems keeping malware off his device. The user
is continuously removing offending apps and regularly running a check for OS updates. After a short
period of relief, the malware continues to be a problem.
Which of the following are the
best actions for the user to take? (Select TWO.)
|
|
|
37.
|
Frank is traveling for work and has discovered that he forgot an important file.
The good news is the file is in cloud storage. Unfortunately, Frank’s laptop cannot connect to
the airport’s Wi-Fi.
How can Frank download this important file? (Select all that
apply.)
|
|
|
38.
|
Which of the following technologies provides a method for personalizing
network-connected laptop and desktop computers with only the apps each individual user needs without
complicated customization? (Select TWO.)
|
|
|
39.
|
A technician is working at a client’s office after hours and needs two
cables to finish the work but does not have immediate access to prebuilt cables. One cable needed is
for a dial-up connection from the dial-up modem to the existing analog POTS jack on the wall. The
other cable is for an Ethernet connection from the computer to the existing keystone jack on the
wall. The technician has the necessary wire and connectors to make the cables.
Which of
the following tools will the technician use to make the cables and then verify that they both work
properly? (Select THREE.)
|
|
|
40.
|
The administrative assistant of the company’s CEO is asking about a
printer for her use only. It seems the shared department printer is overused, making the assistant
wait to print the CEO’s last minute documents.
Which of the following technologies
will best meet the administrative assistant’s request? (Select TWO.)
|
Matching
|
|
|
Match each item with a statement
below. a. | Bluetooth | f. | CPU | b. | POST | g. | DIMM | c. | PCIe | h. | airplane mode | d. | microATX | i. | SO-DIMM | e. | DisplayPort | j. | heat sink |
|
|
|
41.
|
A diagnostic program built into a computer to test the hardware components
before the computer boots up
|
|
|
42.
|
Performs most of the processing for data and instructions for the entire
system
|
|
|
43.
|
Smaller connectors for memory on laptops
|
|
|
44.
|
The standard for computer expansion cards
|
|
|
45.
|
Draws heat away from the CPU or other heat sensitive components so that it can
be dissipated quickly
|
|
|
Match the Optical Drive type to the amount of data the disk will hold.
a. | CD | d. | BD double-side single
layer | b. | DVD single-side single layer | e. | BD double-side dual layer | c. | DVD double-side
single layer | f. | BD double-side
quad layer |
|
|
|
46.
|
4.7 GB
|
|
|
47.
|
25 GB
|
|
|
48.
|
9.4 GB
|
|
|
Match the protocol or encryption name with the feature.
a. | WEP | d. | TKIP | b. | WPA | e. | AES | c. | WPA2 |
|
|
|
49.
|
Generates a different key for every transmission; however, the encryption
algorithm used for its calculations is no longer considered secure.
|
|
|
50.
|
No longer considered secure because the key used for encryption doesn’t
change.
|