Multiple Response
Identify one
or more choices that best complete the statement or answer the question.
|
|
|
1.
|
A technician is working at a client’s office after hours and needs two
cables to finish the work but does not have immediate access to prebuilt cables. One cable needed is
for a dial-up connection from the dial-up modem to the existing analog POTS jack on the wall. The
other cable is for an Ethernet connection from the computer to the existing keystone jack on the
wall. The technician has the necessary wire and connectors to make the cables.
Which of
the following tools will the technician use to make the cables and then verify that they both work
properly? (Select THREE.)
|
|
|
2.
|
Which of the following are secure protocols, ports, services, or applications?
(Select TWO.)
|
|
|
3.
|
The accounting department moved its network-attached printer from one side of
the office to a more centralized location, making the printer much more accessible to all accounting
users. Since the move, the users have not been able to print to the printer. The printer powers on
and shows it is ready to accept print jobs. The printer configuration page shows the following
output. 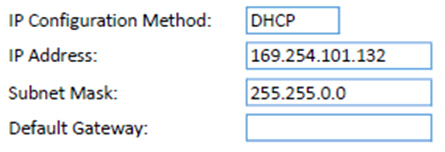 You
disconnect the patch cable from the keystone jack at the new location and move the printer and cable
to reconnect it at the original location. The printer begins printing the jobs that failed to print
earlier. Which of the following are the most likely reasons for the printer failing to
print at the new location? (Select TWO.)
|
|
|
4.
|
A Windows computer is shared between several users, each with his own local user
account. Each user has his own dedicated, uniquely configured VM stored in a public folder on the
computer.
Which of the following steps should be taken to secure the VMs so no user can
copy or delete another user’s VM files? (Select TWO.)
|
|
|
5.
|
The administrative assistant of the company’s CEO is asking about a
printer for her use only. It seems the shared department printer is overused, making the assistant
wait to print the CEO’s last minute documents.
Which of the following technologies
will best meet the administrative assistant’s request? (Select TWO.)
|
|
|
6.
|
Frank is traveling for work and has discovered that he forgot an important file.
The good news is the file is in cloud storage. Unfortunately, Frank’s laptop cannot connect to
the airport’s Wi-Fi.
How can Frank download this important file? (Select all that
apply.)
|
|
|
7.
|
What methods are used to assign TCP/IP parameters to network hosts? (Select
TWO.)
|
|
|
8.
|
A mobile device user is having problems keeping malware off his device. The user
is continuously removing offending apps and regularly running a check for OS updates. After a short
period of relief, the malware continues to be a problem.
Which of the following are the
best actions for the user to take? (Select TWO.)
|
|
|
9.
|
Which of the following technologies provides a method for personalizing
network-connected laptop and desktop computers with only the apps each individual user needs without
complicated customization? (Select TWO.)
|
|
|
10.
|
Molly, a technician, has been tasked with researching an emulator for the
software developers to test cross-platform applications on various PCs and a variety of mobile
devices.
Which of the following will be a required step in selecting an emulator?
(Select TWO.)
|
Matching
|
|
|
Match each item with a statement
below. a. | Bluetooth | f. | CPU | b. | POST | g. | DIMM | c. | PCIe | h. | airplane mode | d. | microATX | i. | SO-DIMM | e. | DisplayPort | j. | heat sink |
|
|
|
11.
|
The standard for computer expansion cards
|
|
|
12.
|
A diagnostic program built into a computer to test the hardware components
before the computer boots up
|
|
|
13.
|
Draws heat away from the CPU or other heat sensitive components so that it can
be dissipated quickly
|
|
|
14.
|
A short-range wireless technology used to connect two devices in a small
personal network
|
|
|
Match the Optical Drive type to the amount of data the disk will hold.
a. | CD | d. | BD double-side single
layer | b. | DVD single-side single layer | e. | BD double-side dual layer | c. | DVD double-side
single layer | f. | BD double-side
quad layer |
|
|
|
15.
|
4.7 GB
|
|
|
16.
|
50 GB
|
|
|
17.
|
9.4 GB
|
|
|
Match the protocol or encryption name with the feature.
a. | WEP | d. | TKIP | b. | WPA | e. | AES | c. | WPA2 |
|
|
|
18.
|
Generates a different key for every transmission; however, the encryption
algorithm used for its calculations is no longer considered secure.
|
|
|
19.
|
No longer considered secure because the key used for encryption doesn’t
change.
|
|
|
20.
|
Current encryption algorithm used today.
|
Multiple Choice
Identify the
choice that best completes the statement or answers the question.
|
|
|
21.
|
Heather’s computer display is having a problem in which the desktop seems
to be shifting. She has sent you a picture of the problem.
?3?
What could be causing this problem on Heather’s
monitor? 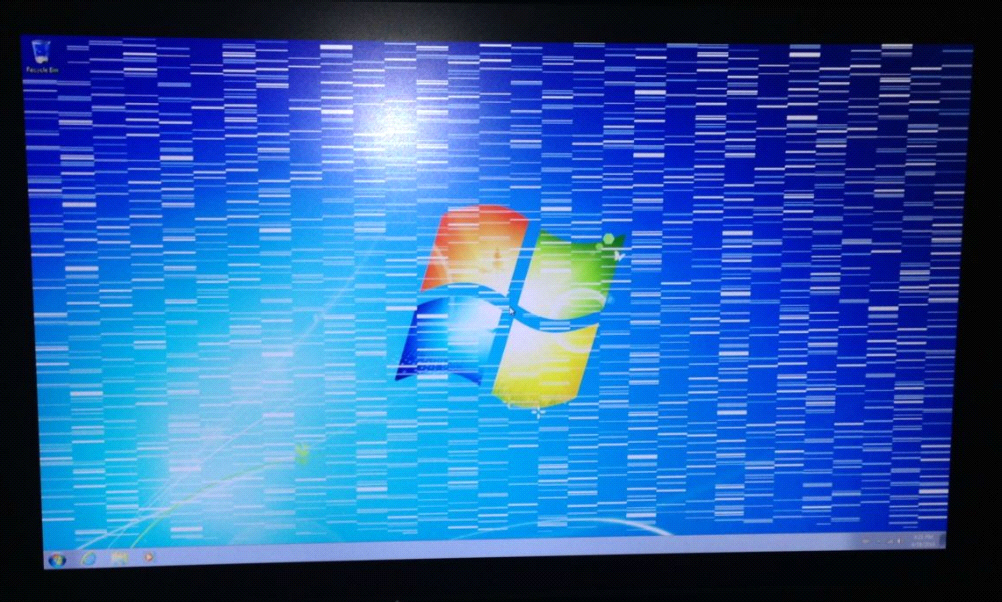 a. | Not enough video memory. | c. | Video cable not properly
seated. | b. | GPU on video card overheating. | d. | Refresh rate out of
specification. |
|
|
|
22.
|
A user is unable to install virtualization software on a Windows 8.1 computer.
The user verified the host has sufficient RAM, plenty of available free disk space, and a multicore
processor.
Which of the following is the most likely cause for this behavior?
a. | The motherboard does not support hardware-assisted virtualization. | c. | Windows 8.1 does
not support Type 2 hypervisors. | b. | The system is incompatible with Type 1
hypervisors. | d. | The user does
not have a valid product license key. |
|
|
|
23.
|
Which of the following creates an environment that behaves in a hardware-like
manner to run software meant for other hardware?
a. | Virtualization | c. | Zero client | b. | Virtual desktop | d. | Emulator |
|
|
|
24.
|
Which of the following is best practice to minimize the chance of infecting your
mobile device with malware?
a. | Keep the device fully charged. | c. | Install apps only from trusted
sources. | b. | Install apps only from untrusted sources. | d. | Perform regular
backups. |
|
|
|
25.
|
Which of the following printer issues is most likely resolved by performing a
calibrate function on a laser or inkjet printer?
a. | Misfeeds (no paper being pulled from the paper tray) | c. | Multiple sheets pulled from the
paper tray at one time. | b. | Misaligned colors on printed
page. | d. | Voids in one or more
colors on a printed page. |
|
|
|
26.
|
Where must virtualization be enabled for VM (virtual
machine) software to work?
a. | BIOS/UEFI | c. | Jumper | b. | TPM chip | d. | Windows Control
Panel |
|
|
|
27.
|
A client is requesting an Internet connection type that is not affected by
atmospheric conditions and is always on.
Which of the following will meet these requirements?
a. | Satellite | c. | Cellular Hotspot | b. | Dial-up | d. | Cable |
|
|
|
28.
|
Jordan has been asked to help his company find a way to allow all the workers to
log on to computers securely but without using a user name and password. The CIO wants everyone use
face recognition software.
What
peripheral will be needed on each computer to allow the workers to log on using face recognition
software?
a. | Face recognition reader | c. | Optical drive | b. | Camera or
webcam | d. | Fingerprint
reader |
|
|
|
29.
|
Roger purchased a new laptop computer and wants to connect it to a second
monitor. The monitor has a DVI and HDMI connection on the back, but his laptop only has a Mini
DisplayPort connection.
?3?
Which cable should Roger purchase?
|
|
|
30.
|
John just bought a used iPad from a friend who had lost the charging cable. John
notices that the cable is like the charging cable for his Android smartphone, though it is not quite
the same.
What type of cable will John need to purchase to replace the iPad’s
charger cable?
a. | Micro USB | c. | USB C | b. | Lightning | d. | Mini HDMI |
|
|
|
31.
|
Jose calls you at the help desk because he is having a problem logging on to his
laptop computer. After several unsuccessful attempts to enter his password, he asks you to reset the
password because he must have forgotten it. You reset his password, and he types it, but again the
computer rejects it. Jose assures you that he typed the correct user name and password. You ask him
what type of computer he is using, and he tells you a laptop.
What might be the problem with Jose’s computer?
a. | OS is corrupt. | c. | Num Lock key is on. | b. | Keyboard is in the wrong
language. | d. | Keyboard is not
working. |
|
|
|
32.
|
When is it okay to touch the inside of a computer
that is turned on?
a. | When using a multimeter to measure voltage output | c. | When a qualified electronics expert
or electrician is present | b. | When reassembling the
computer | d. | When disassembling
the computer |
|
|
|
33.
|
What type of RAM is typically installed onto a
motherboard and loses data rapidly, requiring it to be refreshed often?
a. | SRAM | c. | DRAM | b. | CMOS RAM | d. | Flash RAM |
|
|
|
34.
|
Lin is booting up his computer, and during the boot process, the computer powers
down. After several unsuccessful attempts to boot his computer, he decides that he needs to start the
troubleshooting process. Lin thinks that the problem could be in the power supply, so he uses a power
supply tester. The test shows that the power supply is functioning properly.
What should Lin check next in the troubleshooting
process?
a. | Motherboard | c. | RAM | b. | Processor | d. | Hard drive |
|
|
|
35.
|
You have been tasked with configuring a SOHO network in which all ports on the
public untrusted network will be forwarded to one workstation connected to the LAN.
Which of the following features will you configure on the
SOHO router to accomplish this task?
a. | Demilitarized zone | c. | MAC filtering | b. | Port forwarding | d. | Quality of
service |
|
|
|
36.
|
Gina is upgrading your computer with a new processor. She installs the processor
into your motherboard and adds the cooling system. She powers up the computer, and it begins to boot
but then shuts down.
What could be the cause of this
problem?
a. | Processor is not seated properly | c. | Thermal paste was not
used | b. | Processor is not compatible | d. | Computer is overclocked |
|
|
|
37.
|
Reggie has hired you to design a home network. The home network will share a
printer but will mainly be used to stream movies to two different rooms.
What kind of storage should you recommend to Reggie for this
type of network?
a. | Magnetic hard drive | c. | Network-attached storage | b. | Cloud
storage | d. | SSD hard
drive |
|
|
|
38.
|
What is a possible remedy if your system hangs at
odd times or during the boot?
a. | Flash the BIOS/UEFI | c. | Format the hard disk | b. | Remove the TPM chip | d. | Install new CMOS
RAM |
|
|
|
39.
|
Mary, a remote user, connects her Windows 10 laptop to the corporate network by
way of the Internet using a VPN tunnel.
Which of the following is often configured as a required step
for a user each time she attempts to use the VPN connection?
a. | Call the help desk at the corporate office to obtain a random VPN
password. | c. | Select the encryption and authentication methods in Connection
Properties. | b. | Configure the laptop to a static IP address on the corporate LAN
subnet. | d. | Enter the same user
name and password used on the corporate network. |
|
|
|
40.
|
Which of the following represents a method for
accessing the BIOS/UEFI setup program?
a. | Set a motherboard jumper and start the computer | c. | Boot to the BIOS setup floppy
disk | b. | Press a key or combination of keys during the BIOS/UEFI POST | d. | Boot Windows and go to Control
Panel |
|
|
|
41.
|
A mobile device you are troubleshooting is experiencing a sharp decrease in
performance after an hour of operation. The user powers the device off each evening, and when it is
powered on, performance returns to normal. After an hour of operation, performance
degrades.
Which of the following is the best action to take to resolve this
issue?
a. | Update the mobile device firmware. | c. | Adjust the brightness
control. | b. | Reset the device to factory defaults. | d. | Close or disable all unused running
apps. |
|
|
|
42.
|
Landon starts his computer and receives the error message, “Hard drive is
not found.” In a panic, he calls you because he did not back up his data and has numerous
important files on his hard drive. During your investigation, Landon tells you he was watching a
movie on his computer the previous night.
What might be the problem with Landon’s
computer?
a. | POST failed | c. | Motherboard needs to be replaced | b. | CMOS RAM has lost
power and reset to defaults | d. | Boot priority is set to the DVD drive |
|
|
|
43.
|
Which of the following indicates the most concise abbreviation of the IPv6
address FEFE:0000:0000:0000:0002:0000:0000:0001?
a. | FEFE::0002:0000:0000:0001 | c. | FEFE::2:0:0:1 | b. | FEFE::2::1 | d. | FEFE:0:0:0:2:0:0:1 |
|
|
|
44.
|
A manager in a small office is asking if it is possible to limit network access
to a particular website during business hours. Apparently, several users are spending an excessive
amount of time on the site preventing them from completing their work-related tasks.
Which of the following is the best solution to accomplish the
request from the manager while not limiting access to other websites?
a. | Configure a firewall with content filtering on the PCs of users who are visiting the
site. | c. | Implement a blacklist on the firewall and add the site the users are
visiting. | b. | Implement MAC filtering on the SOHO router for the PCs that are accessing the
site. | d. | Configure a firewall
and add the site the users are visiting to the whitelist. |
|
|
|
45.
|
When you are ordering a standard thick client computer for a normal business
user, what should you check before ordering the computer?
a. | Amount of RAM. | c. | Amount of storage available. | b. | Meet requirements
for the OS. | d. | Speed of
CPU. |
|
|
|
46.
|
Which setting can be configured via the BIOS/UEFI
screen?
a. | Windows driver status | c. | Change the boot sequence | b. | Set desktop
background | d. | Screen saver
timeout value |
|
|
|
47.
|
Your mobile device appears to be contacting a remote server to upload your
personal data.
Which of the following should be performed first to protect your personal
data?
a. | Verify you are on the correct Wi-Fi network. | c. | Install anti-malware
software. | b. | Switch to airplane mode. | d. | Perform a factory reset. |
|
|
|
48.
|
You are troubleshooting a mobile device that will not pair with a Bluetooth
headset. The device was functioning properly with the headset until a recent corporate-wide OS
update. No other mobile devices in the organization are exhibiting this issue with Bluetooth
headsets.
Which of the following is the first step you will take to resolve this
issue?
a. | Forget all Wi-Fi networks on the mobile device | c. | Update the radio firmware in the
mobile device. | b. | Reset the network settings in the mobile device Settings app. | d. | Replace the Bluetooth headset with a new
pair. |
|
|
|
49.
|
A processor housing that contains more than one
processor is referred to as what term?
a. | Multihoused processor | c. | Multicore processor | b. | Multiprocessor platform | d. | Multithreaded
processor |
|
|
|
50.
|
Mark has been asked to set up several smartphones to connect to his
company’s email server. The company wants Mark to set them up so they can be synchronized
between multiple email clients on multiple devices.
What protocol should Mark use to set
up the company smartphones?
a. | Bluetooth | c. | IMAP | b. | VPN | d. | POP3 |
|